
Solutions
DeepTruth’s frameworks do not focus on defensive forensic techniques to “identify-and-discredit” counterfeits – we go on the offense and construct images, videos, and audio recordings that are impossible to manipulate without detection.
Solutions
DeepTruth’s frameworks do not focus on defensive forensic techniques to “identify-and-discredit” counterfeits – we go on the offense and construct images, videos, and audio recordings that are impossible to manipulate without detection.
“Soon, it’s going to get to the point where there is no way that we can actually detect [deepfakes] anymore, so we have to look at other types of solutions.” – Hao Li, Professor at University of Southern California
How DeepTruth Works
DeepTruth’s multi-patented framework records unbreakable media by constructing cryptographic DNA fingerprints – in real-time. The DNA maps every pixel, sound bite, and frame while simultaneously layering content attribution analytics and metadata.
The DNA is preserved, during recording, in an immutable distributed blockchain ledger.
The integrity and authenticity of digital assets can be verified, at any time, by reconstructing the digital DNA fingerprints and comparing it to the original DNA. If any sub-second of a digital asset has a single pixel modified or sound bite altered or any of the dimensions of content attribution data changed, it will be flagged.
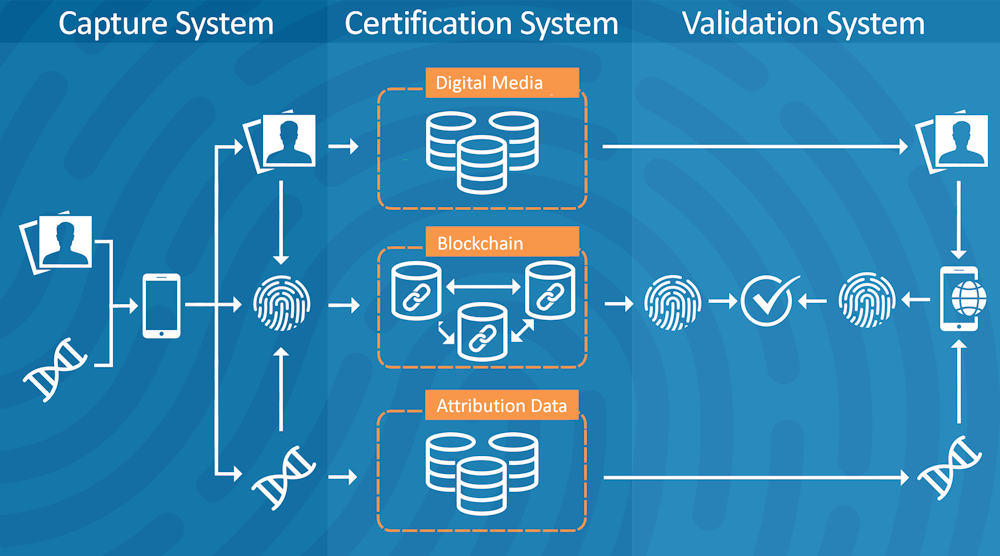

How It Works
DeepTruth’s multi-patented framework records unbreakable media by constructing cryptographic DNA fingerprints – in real-time. The DNA maps every pixel, sound bite, and frame while simultaneously layering content attribution analytics and metadata.
The DNA is preserved, during recording, in an immutable distributed blockchain ledger.
The integrity and authenticity of digital assets can be verified, at any time, by reconstructing the digital DNA fingerprints and comparing it to the original DNA. If any sub-second of a digital asset has a single pixel modified or sound bite altered or any of the dimensions of content attribution data changed, it will be flagged.
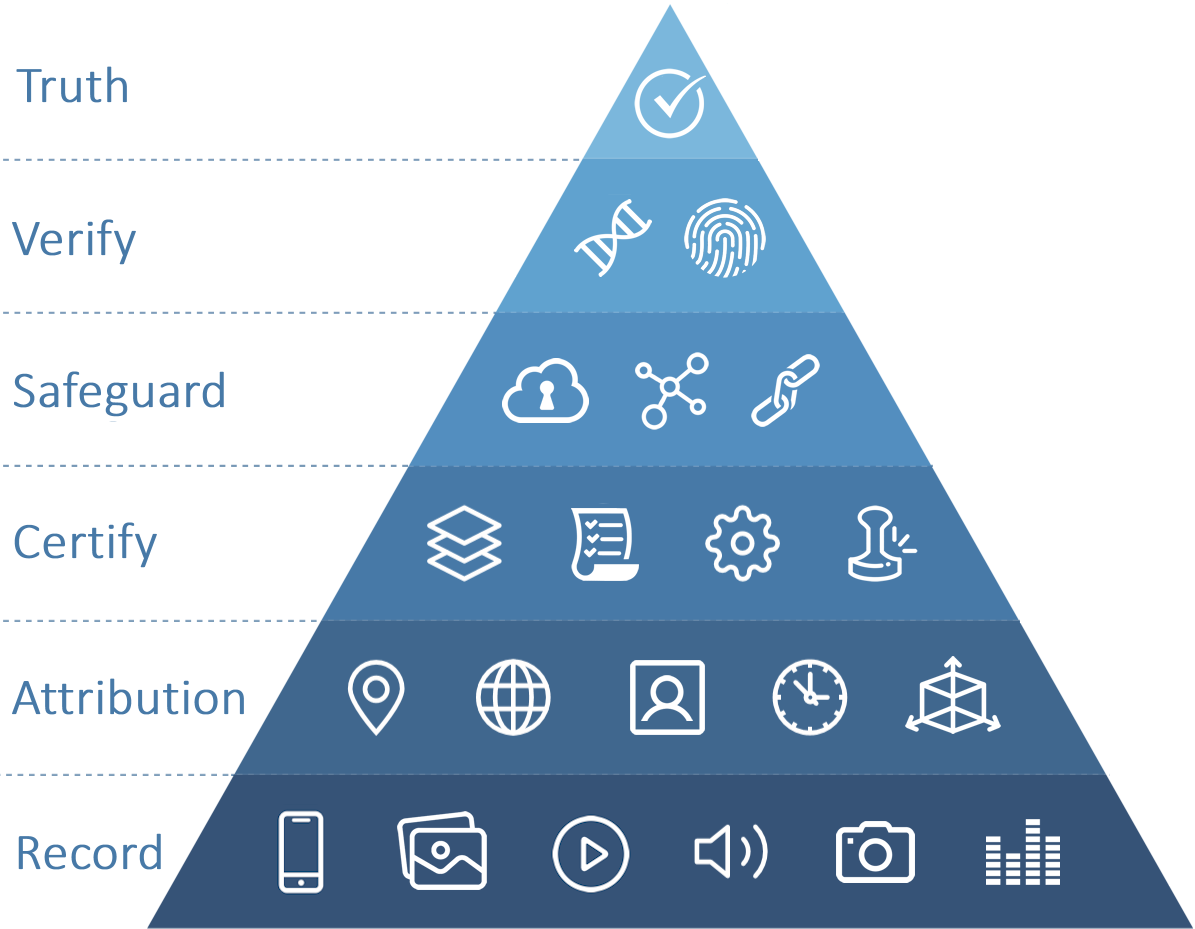
Why DeepTruth Is Unbreakable
DeepTruth constructs images, videos, and audio recordings that are impossible to modify without detection because of these requirements:
Establishing credibility must occur during recording. All visual and audio elements must be cryptographically mapped and layered with attribution content to construct DNA fingerprints – in real-time.
Maintaining integrity requires the DNA fingerprints to be securely distributed to an immutable distributed ledger (blockchain) system.
Proving authenticity demands absolute perfection. Every frame, pixel, sound bite, and all dimensions of attribution must be a precise match.
Privacy is maintained because the digital media does not leave the recording system – digital asset are protected in-place.

Why Unbreakable
DeepTruth constructs images, videos, and audio recordings that are impossible to modify without detection because of these requirements:
Establishing credibility must occur during recording. All visual and audio elements must be cryptographically mapped and layered with attribution content to construct DNA fingerprints – in real-time.
Maintaining integrity requires the DNA fingerprints to be securely distributed to an immutable distributed ledger (blockchain) system.
Proving authenticity demands absolute perfection. Every frame, pixel, sound bite, and all dimensions of attribution must be a precise match.
Privacy is maintained because the digital media does not leave the recording system – digital asset are protected in-place.
Why DeepTruth Is Different
The predominant efforts by leading tech companies have focused on forensic techniques to identify-and-discredit counterfeit content. Unfortunately, the sophistication of synthetic media will continue to outpace various defensive efforts.
The only solution to permanently defeat synthetic media is to go on the offense. Every video, image, and audio must be recorded and protected, end-to-end, in a manner that makes them impossible to modify or manipulate without detection.
DeepTruth is the solution.


Why It’s Different
”Soon, it’s going to get to the point where there is no way that we can actually detect [deepfakes] anymore, so we have to look at other types of solutions.” – Hao Li, Professor at University of Southern California
The predominant efforts by leading tech companies have focused on forensic techniques to identify-and-discredit counterfeit content. Unfortunately, the sophistication of synthetic media will continue to outpace various defensive efforts.
The only solution to permanently defeat synthetic media is to go on the offense. Every video, image, and audio must be recorded and protected, end-to-end, in a manner that makes them impossible to modify or manipulate without detection.
DeepTruth is the solution.
